Privacy-enhancing Bitcoin-compatible protocols
Nowadays, privacy has become such an important topic within the many technologies we use in our lives that it’s only natural for us to ask the question: Where does privacy stand in the world of cryptocurrencies? The intuitive answer of many people unfamiliar with blockchain technology is that cryptocurrencies provide full anonymity and privacy. Similarly to a famous pawnshop owner bargaining on their tv show: “Anonymity? Sorry, best I can do is pseudonymity.”
As a starting point, let’s define what anonymity means in the context of cryptocurrencies. The term could be explained as the sum of pseudonymity and unlinkability.
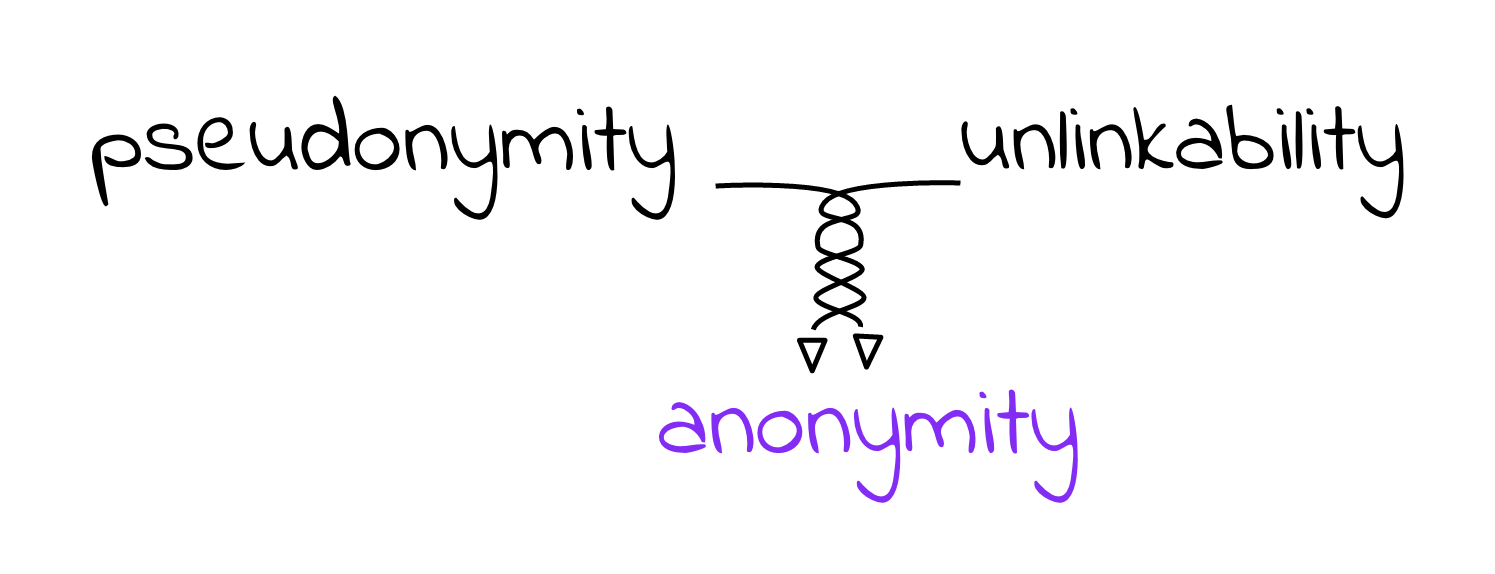
Those two concepts are very closely intertwined and it’s important to point out that the latter isn’t simply a nice-to-have rather an essential part. I’ve heard many times the incorrect assumption that even if one’s pseudonyms (blockchain addresses) are linked, how could that possibly lead to the person behind those pseudonyms. In reality, many cryptoasset services hold some kind of personal identifiable information (PII). All it takes is one pseudonym to be linked to the PII and the thread unravels. Let’s take a closer look at the most famous cryptocurrency – Bitcoin and why it’s not fully anonymous.
- Firstly, cryptoassets built on a blockchain are public and that includes both transactions and addresses.
- Secondly, addresses could be linked via clustering heuristics used in different tools such as Chainalysis, CipherTrace, and GraphSense.
- Lastly, as previously mentioned, many cryptoasset services hold PII that lead back to the people behind addresses.
All of these points lead to the fact that transactions along with senders and recipients of payments could be linked to specific users. It’s easy to see that Bitcoin is missing the unlinkability part from the anonymity equation. Not only that but also the offered privacy is arguably worse than that of traditional banking. In the end, the underlying blockchain put together with the data saved from different exchanges creates somewhat of a privacy hell.
I think that at this point we can agree that although the early promises and expectations from cryptoassets were for anonymity, linkable payments are the de facto status quo. Looking back at more than a decade of cryptoassets, we can observe an ever-increasing acceptance of cryptocurrencies as means of payment. However, with great power comes great responsibility. On the one side, there’s the positive increase in acceptance, while on the other side there are all of the negative news throughout the years: the shutdown of the Silk Road Darknet Marketplace, the famous Mt. Gox hack, the Bitstamp security breach, the DAO hack, the wave of Ponzi schemes and ICO scams. If you ask me, those events are inevitable for a new and emerging technology in the field of payments. Just like every new creation there still are a lot of unknowns and problems that should closely be analyzed and solved.
In that spirit, let’s look at the opportunities to avoid linkability in cryptocurrencies. The first approach I will analyze is the application of Bitcoin-compatible solutions.
Coin mixing
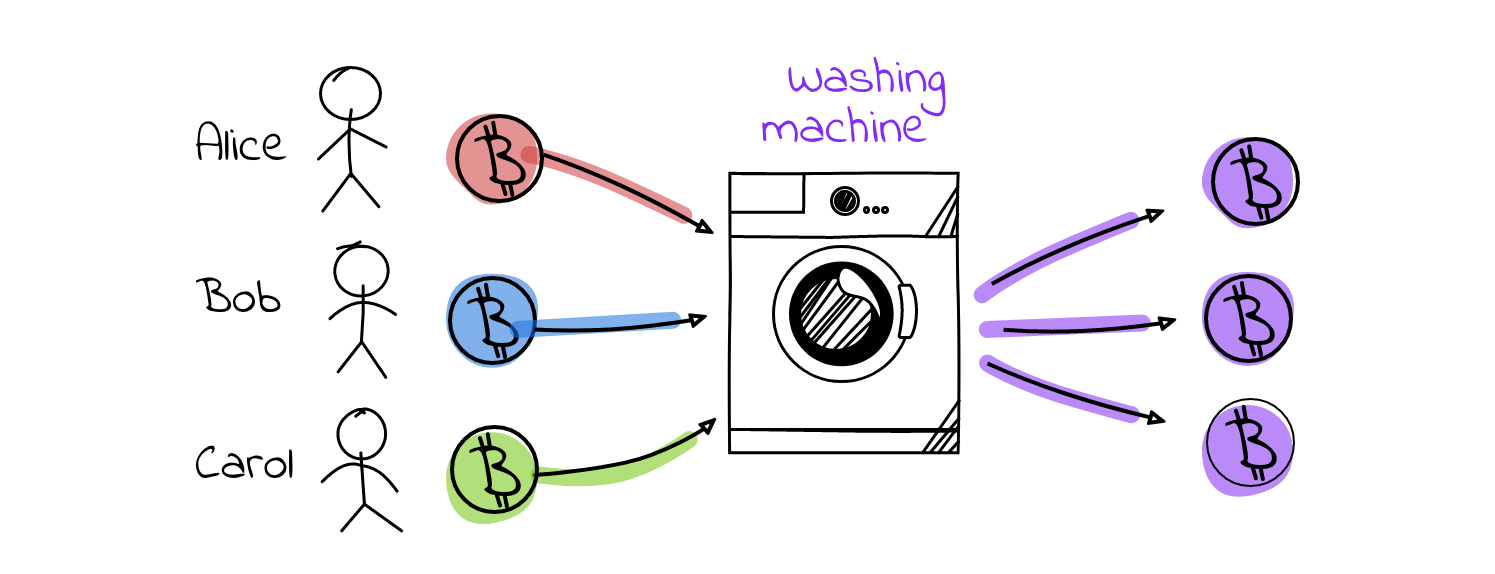
The basic idea of coin mixing is quite straightforward. An arbitrary amount of honest users each put the same amount of “tagged” coins as input in the mixer and wish to obtain that amount of “untagged” coin if the mixing was a success or receive back the original “tagged” coins if the mixing failed due to some reason. Of course, the described process sounds intuitively like a centralized service of sorts. There are several issues with that: the mixing service can always link coins to users and it’ll almost surely require some kind of fee. We can also mention theft by the service as a potential issue although there are protocols that can make the mixing service accountable for the number of coins (BNMCKF Mixcoin proposal). An example for a centralized trusted mixing service is bestmixer and for an untrusted mixing server – TumbleBit. Great, now that the shortcomings are pointed out, the logical question is: What about decentralized solutions?
Decentralized mixing sounds great due to several reasons. There is no central service, theft is impossible, it provides inherently better anonymity and lastly, it follows Satoshi Nakamoto’s decentralized philosophy for Bitcoin.
CoinJoin
The first decentralized mixing protocol to mention is the CoinJoin protocol. I’ll try to make a very short and non-technical summary of the protocol and if you feel it’s unjust, please excuse me. The first step is to find users who also want to mix the same amount of coins as you. After that, you exchange input and output addresses for the transactions. Every user constructs their transaction (where does the user want to send coins to), sends it around, collects signatures from the other users, and before signing (confirming the transaction) also checks that their output is present. After that, the transaction with the inputs and outputs is broadcast to the Bitcoin network. So far, this protocol fulfills the decentralization and no-theft requirements. However, it introduces another big problem. That is, if a malicious user “infiltrates” the CoinJoin group, then that user knows the input/output combinations of all the other users and has no problem sharing that information with someone else.
CoinShuffle
This is where an improved protocol called CoinShuffle comes into play. CoinShuffle’s main improvements are that it provides unlinkability (input/output combinations aren’t linkable to users) and robustness (if there’s a malicious user, they will be exposed). CoinShuffle functions similarly to a pinboard where users willing to participate indicate that by generating cryptographic key pairs and posting the public key. It’s important to note that CoinShuffle can guarantee unlinkability and robustness as long as there are at least 2 honest users on the board. The protocol itself has two main building blocks – layered encryption and permutation that ensure it can work as intended.
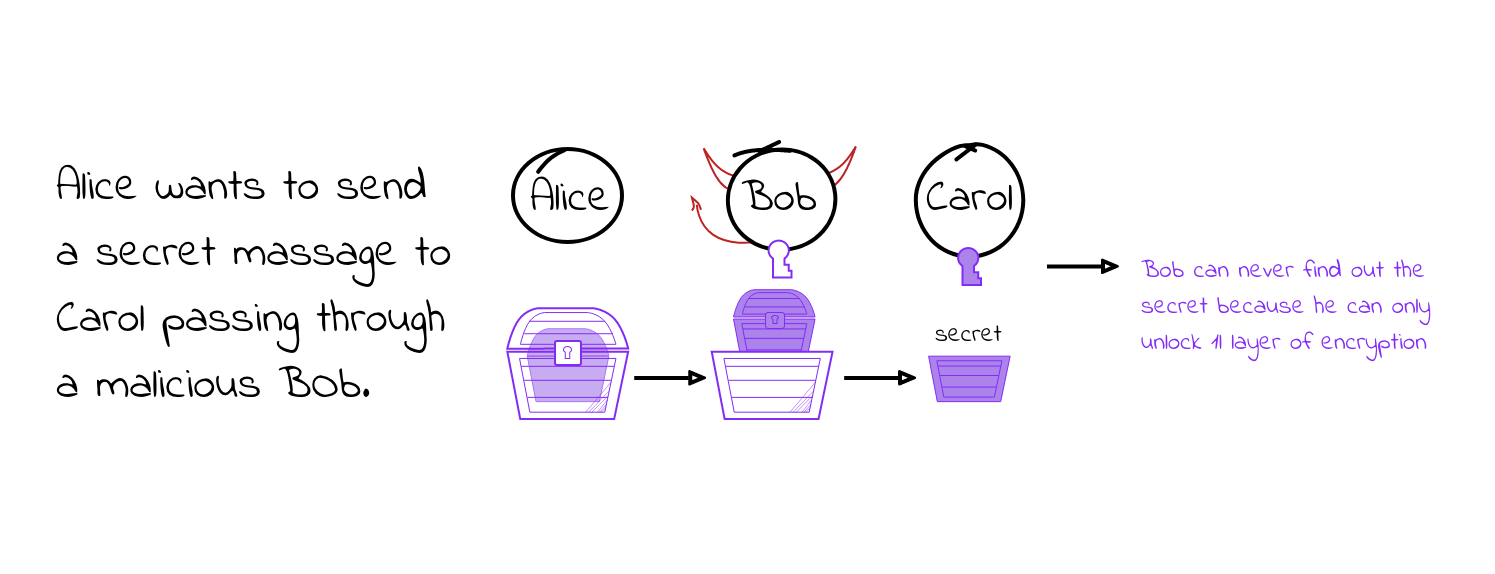
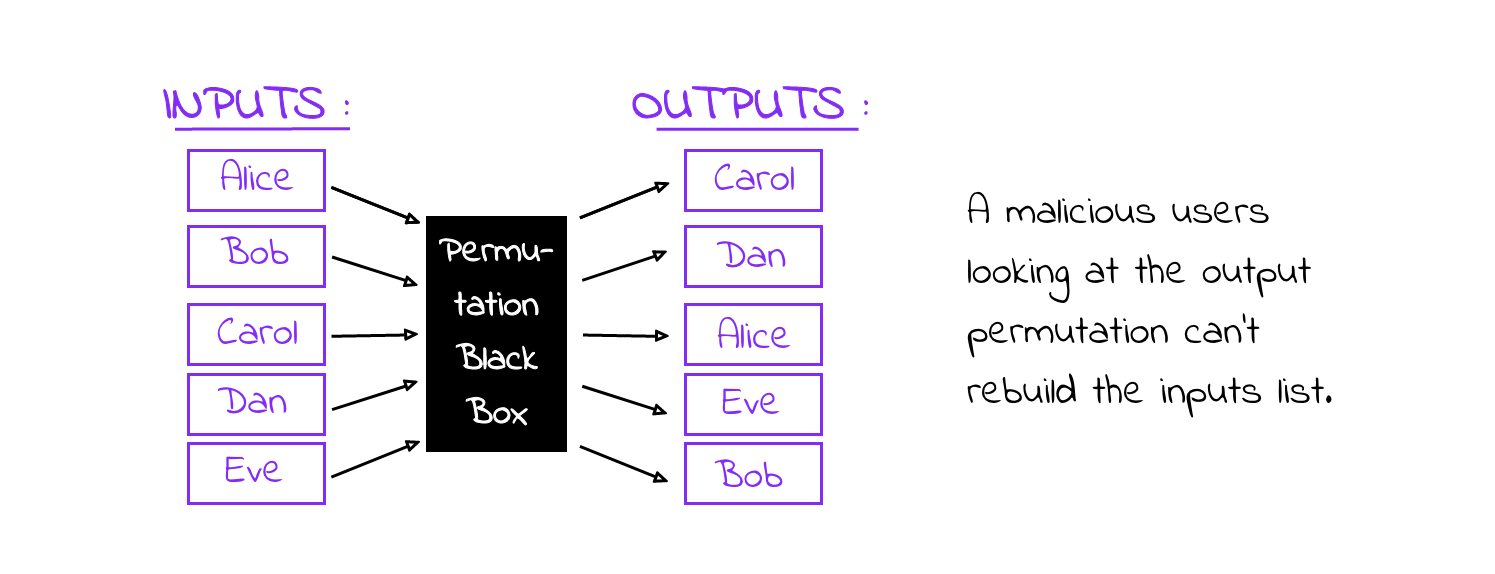
So, once the protocol is initiated, each user generates an output address and has to use the key pair with which the user “joined” the board. After that, each participant uses their signature key to sign their input address + public key and post that to the board. Then, each user applies onion encryption to their output address using the public keys of the “upcoming” users and adds that to the chain of encrypted output addresses. The idea is that the different encrypted output addresses are indistinguishable by the other users since they could decrypt only one layer and so, in the end, no user can link any output address to a specific user.
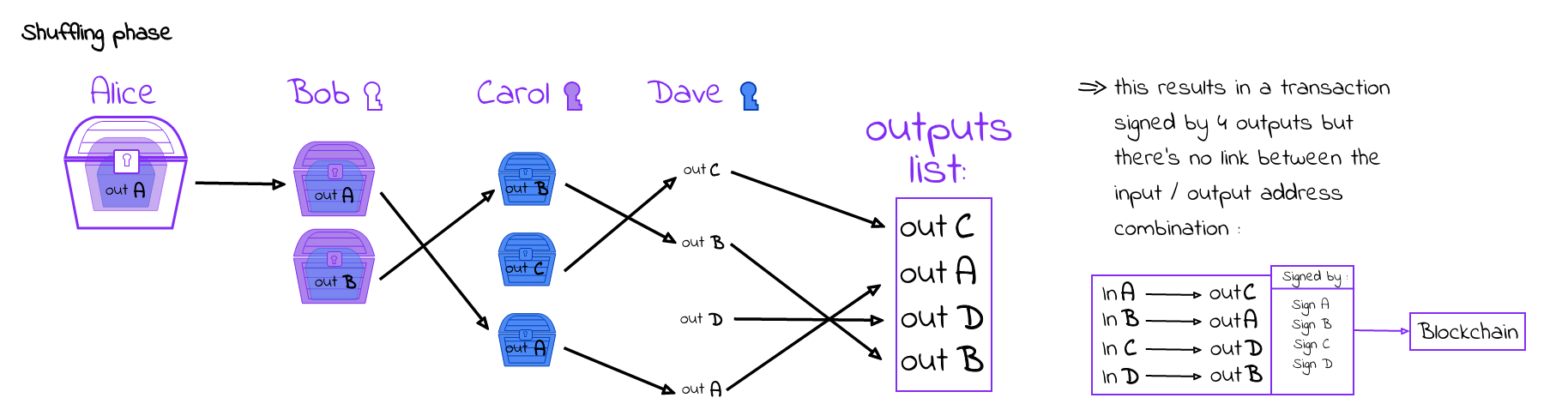
As for the robustness, there’s no guarantee that a malicious user wouldn’t just refuse to sign the transaction when it’s their turn and thus force the mixing to fail. There is, however, a solution for that situation as well and it’s called the blaming phase. Since the cryptographic key pair used to “post” on the pinboard is created only for the current transaction, it’s no problem to reveal all private (decryption) keys in the case of a failed transaction. Following the reveal, all encryption steps are replicated and the “malicious” user whose private key is missing can be exposed and kicked from the protocol. After that, the protocol should force the remaining participants to create new Bitcoin addresses and cryptographic key pairs for improved privacy before running again.
After covering those two protocols in a somewhat informal manner, we can conclude that there’s a real possibility to enhance the privacy of Bitcoin transactions while remaining fully compatible with the currency. It is safe to say that what applies to Bitcoin, can generally be used for a great number of other cryptocurrencies as well. You might be impressed by the improvement in privacy a protocol can bring and naturally ask yourself: “Well, if the protocol’s so great, why isn’t it the norm?”
That’s simple – users can decide for themselves to ignore it and simply use the cryptocurrency as originally designed. No one can enforce the usage of privacy-enhancing protocols on a global scale. Some wallets implement them, nevertheless, a lot of users decide to perform their transactions in a “vanilla” fashion with the idea that they don’t have anything to hide so they have no problem with their transactions being linkable. Whether that’s a correct approach or not, everyone can decide for themselves. The main point is to not lose sight of the importance of privacy in today’s world and that includes the ever-growing field of cryptocurrencies.
Regardless of whether you agree with the previous statement or not, there are already solutions that try to combat the inherent privacy issues found in Bitcoin and other cryptoassets. They achieve this by taking a step further than the privacy-enhancing protocols and building new cryptocurrencies with privacy at their cores. Those privacy-enhanced cryptocurrencies try to correct flaws in other cryptoassets at the cost of being inherently more complex and not having backwards compatibility. Prominent examples are Monero, Zerocoin, and Zerocash. They implement interesting improvements over older cryptocurrencies and will hopefully, continue to grow. In the second part of the blog post, we will dive deeper into their details to further clarify the possibilities of keeping your data private in the world of cryptocurrencies.
![Cover Image for Cryptocurrencies and privacy [part 1]](/_next/image?url=https%3A%2F%2Fwp.web.hack.bg%2Fwp-content%2Fuploads%2F2021%2F04%2FCover-1.png&w=3840&q=75)


